
Test A-R53-11 specifically looks for Domains that do not have a transfer lock enabled. A transfer lock is nothing more than an additional step ahead of transferring a domain to ensure a “belt & braces” type confirmation that a domain should definitely be transfered. All a transfer lock requires is that the transfer lock is disabled by an API call or a confirmation in the AWS Web Console ahead of initiating a transfer. However, this simple mechanism provides a few additional features to help protect domains from being stolen, even to insiders.
reference security domains
SkySiege tests A-S3-4, A-S3-5, A-S3-6, A-S3-7, A-S3-8 and A-S3-9 all focus on public access blocks and the quality of S3 Bucket Policies. The reasoning for this is simple - Public Access Blocks and Bucket Policies are front line protections for ensuring that your data is not publicly available.
reference security domains

Test A-R53-10 reviews DKIM records to determine if the DKIM key is of a suitable size. As the DKIM key is part of a asymetric keypair we can infer certain properties of the corresponding private key, including the key size. Therefore using small key sizes for DKIM signatures publicly advertises that your private key must also be a small size and therefore subsceptible to cracking.
The researchers at Jedi Security successfully cracked a 512-bit DKIM key and were able to forge an email with the cracked key which successfully passed DKIM checks across a number of top email service providers.
reference email domains
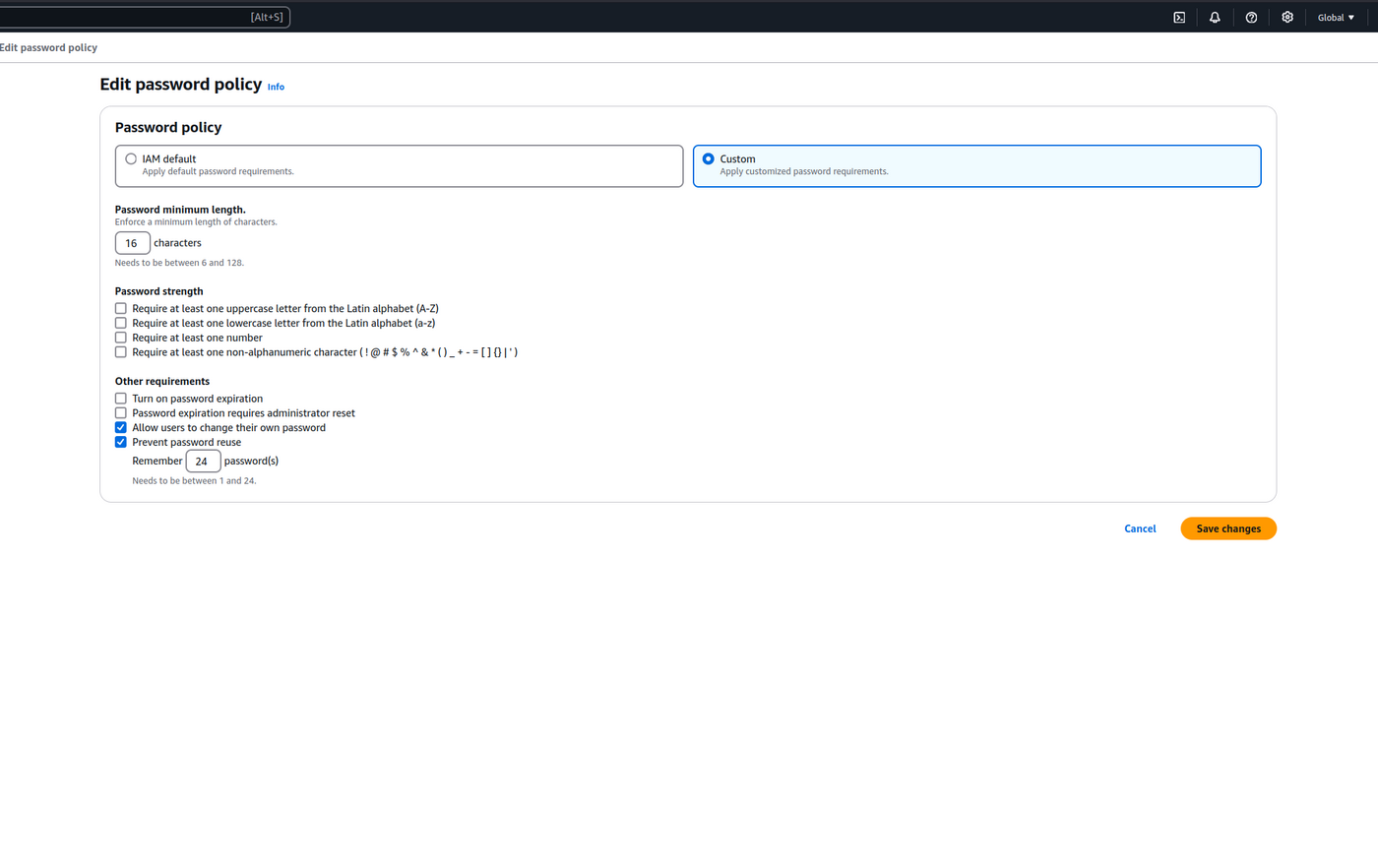
The AWS Password Policy dictates the security standards and management of AWS IAM User passwords used for access to the AWS Console. We extend the default policy to increase security and minimise additional processes providing the most efficient password management configuration we can design.
cspm cloud guidance
Test A-R53-8 specifically looks for Domains that are due to expire within the next 90 days that do not have any form of auto renewal. We reference the risk for expired domains to get squatted whereby a third party captures the domain and utilises it for ransom, SEO capture or other nefarious schemes. However, there’s an additional level of risk in the data that the domain has implicit ownership over that has been proven by other researchers in the field.
reference security domains

An AWS security assessment evaluates the security posture of an AWS account, analysing the cloud resources contained in an account and their configuration. The goal of this assessment is to find any resources or vulnerabilities that can be maliciously utilised to compromise any services hosted in the AWS Account. Minimising these vulnerabilities will result in the hosted services being more resilient to attack and therefore adopting a stronger security posture.
vulnerability scan cloud aws

In our previous article, we explored the benefits of adopting a multi-cloud architecture. In this article, we’ll deliver as promised some introductory architectures that can serve as your starting point for adopting a multi-cloud infrastructure.
multicloud security architecture

Leveraging multi-cloud technologies and architectural patterns is becoming an increasingly important part of modern technology architecture. Whilst multi-cloud approaches offer numerous advantages, they also add complexity resulting in an expanded knowledge burden, additional access controls and an absence of replicable patterns.
multicloud security architecture

If you are hosting applications on Amazon Web Services (AWS), it is important to consider the impact to AWS from your penetration testing. A key aspect of this consideration is determining whether what penetration testing can be safely conducted on the AWS platform without advanced permission and which testing should be abstained from without prior agreement.
penetration testing cloud aws
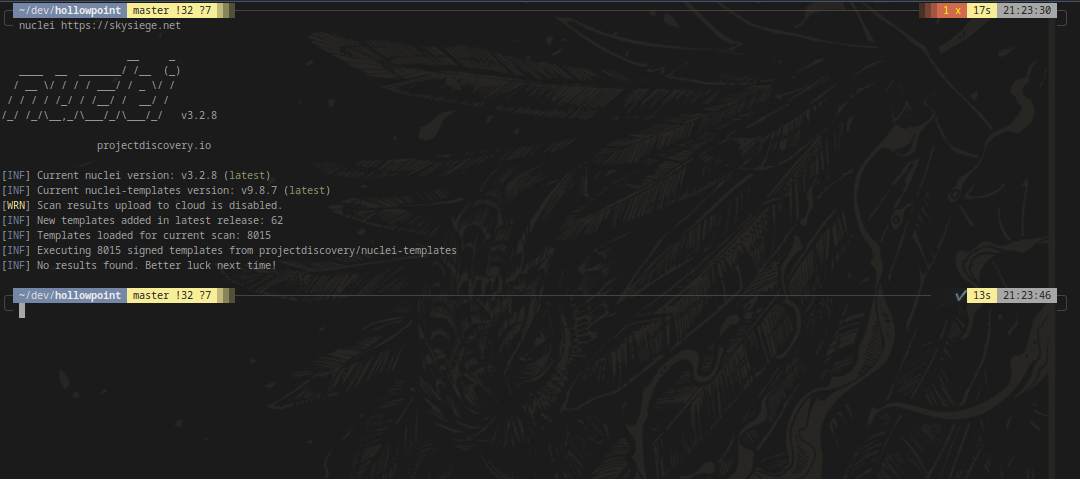
Automated penetration testing differs from regular penetration testing by utilising a set of tools and services that continuously test applications to identify and exploit both new and old vulnerabilities. Most tools available in the cloud and application security space have some level of automation, with some tools operating entirely automatically, requiring a small number of initial commands and configuration. These automated tools handle various components of the testing process, such as discovery, identification, scanning, and simulated attacks.
penetration testing cloud automation